Case Study
Introduction
We run a niche online store targeted exclusively to North American customers. Occasionally, we have sales from IP addresses outside our market area, which we assume are from Americans traveling abroad since we ship our products only to the US and Canada.
Our infrastructure
We have two Windows Server 2019 Core servers collocated in the US. Both are connected to the Internet, plus they are interconnected by a private crossover connection. The first server is a Web server with open website ports 80 and 443 and administrative ports 6516 for Windows Admin Center and 22 for SSH. The other server runs the database and is only open on the admin ports.
How we configured IPBlock for our environment
Website firewall filters
First, we created our IP sets. The main set we called "S_Website_Normal" is intended for filtering traffic on our Web ports under normal conditions. For this set, we blocked all the countries except the USA, Canada (our customer base), and the countries in Europe, the Caribbean, Mexico, Japan, and some others where we assume our customers are likely to travel. We also blocked Datacenters to prevent extra load on our servers and Compromised Computers lists:
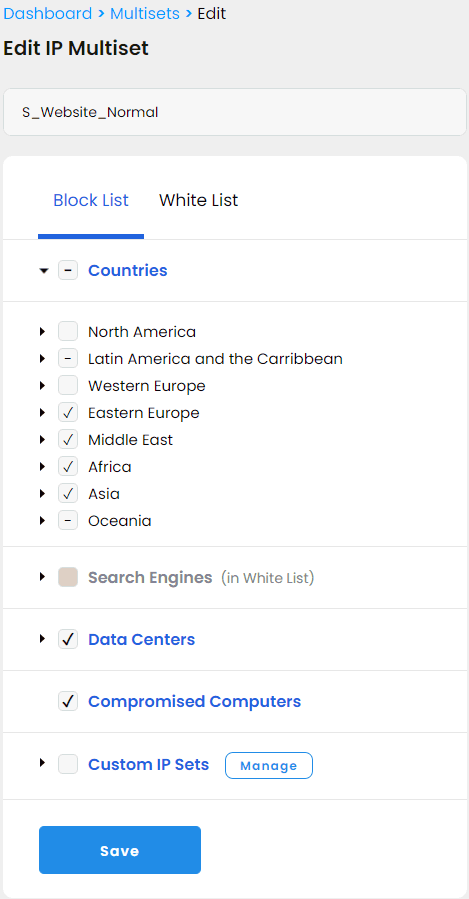
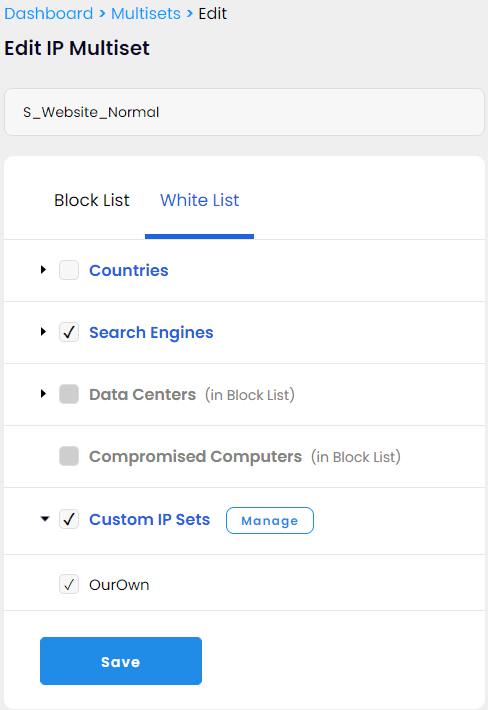
To make sure we do not block any search engines from indexing our website we added them to the White List. We also added the custom set of our own IP addresses, just to be safe:
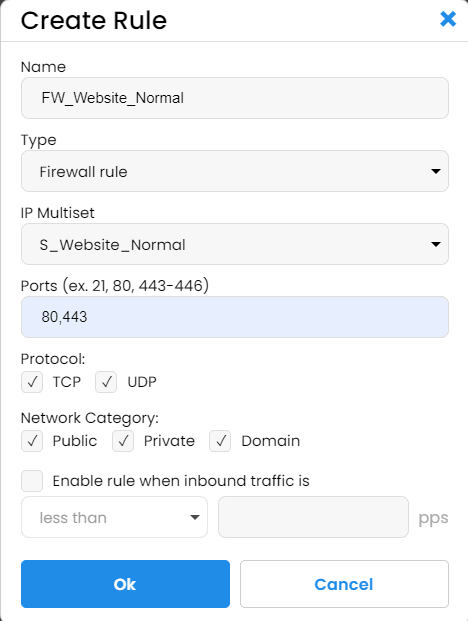
Next, we created a firewall rule which we called "FW_Website_Normal" with "S_Website_Normal" IP set as:
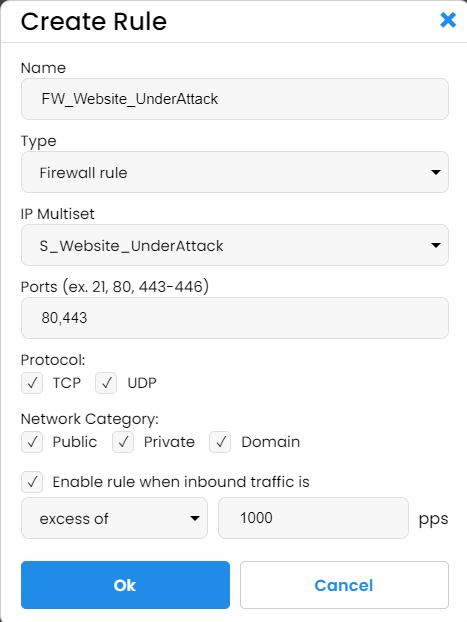
As our next step, we decided to create a more restrictive filter for our website traffic in case we have an abnormal number of requests. For this, we created another IP multiset named "S_Website_UnderAttack." It is similar to "S_Website_Normal" but blocks all the countries other than the US and Canada and all the search engines except for Google, Bing, and social bots.
The firewall rule we called FW_Website_UnderAttack and created with similar settings, but we set it to activate only if the incoming traffic exceeds 1000 packets per second, roughly ten times our normal peak volume:
Admin port filters
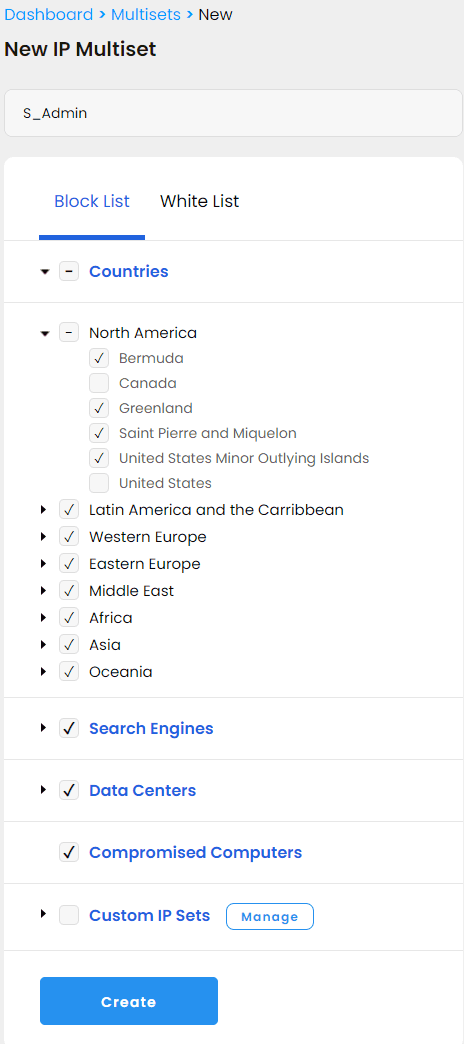
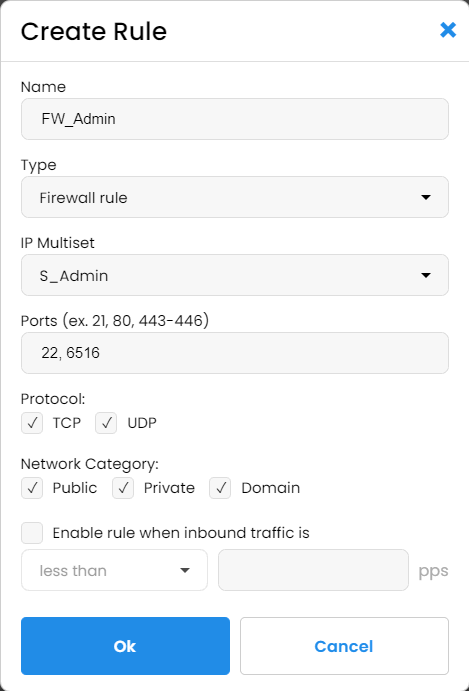
For the admin access, we created the most restrictive IP multiset "S_Admin" and blocked all the countries except the US and all the search engines and compromised computers. We whitelisted nothing except for our own IPs:
The new rule FW_Admin we created is straightforward:
Connecting the servers
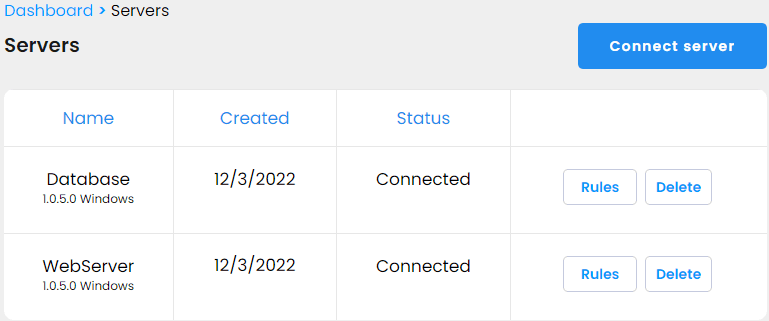
In our next step, we installed the IPBlock client software on our servers using the instructions for Windows Core servers:
Putting it all together
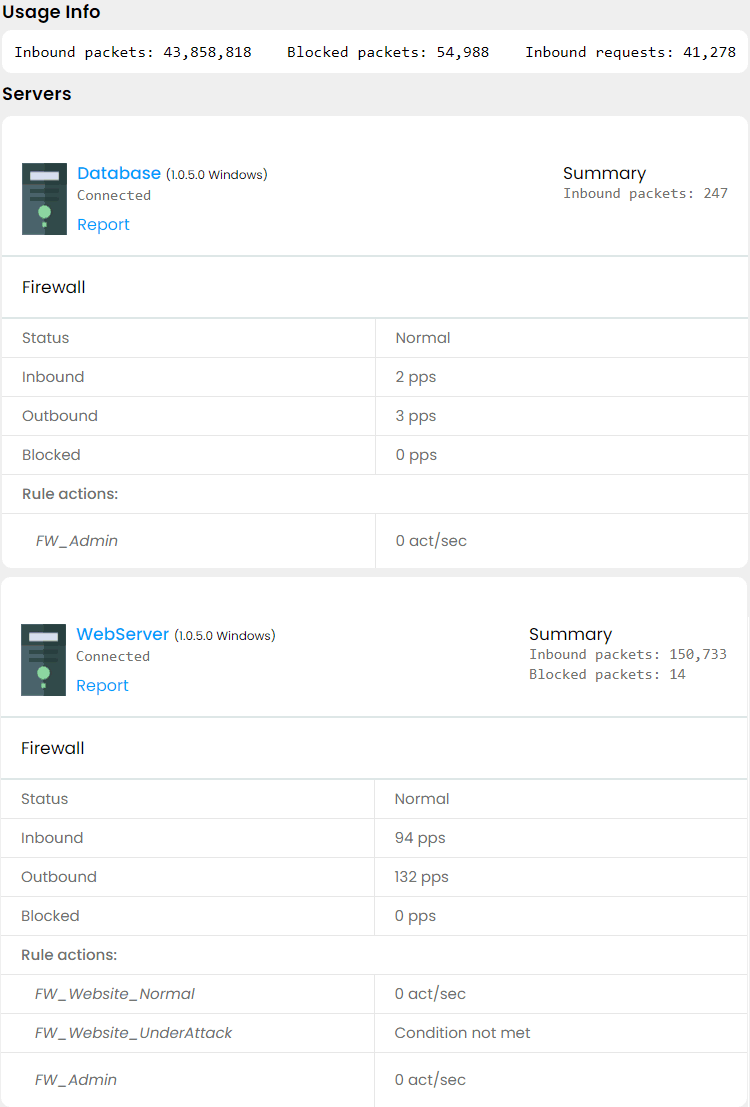
As the final step, we attached the rules to the servers. To the Web server we attached all our three rules, to the Database server — only the Admin rule.
And finally, this is our Dashboard with everything in place: